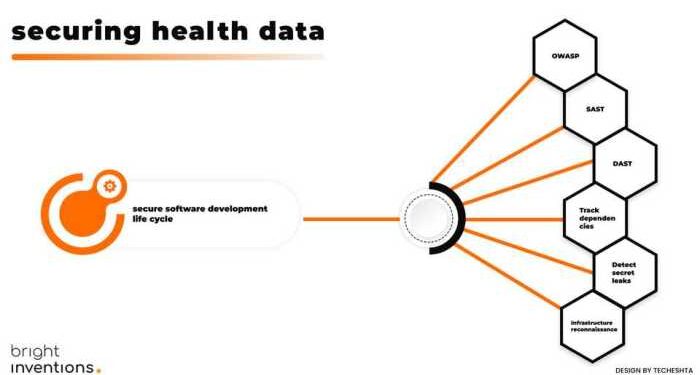
Embark on a journey through the realm of securing health data with cloud technology, where the stakes are high and the need for robust protection is paramount. As we delve into the intricacies of safeguarding sensitive information, a tapestry of best practices unfolds to guide healthcare organizations towards a secure future.
Explore the nuances of encryption, access control, data backup, and incident response as pillars of defense in this digital landscape, where compliance regulations serve as beacons of accountability and security.
Importance of Securing Health Data
In today's digital age, securing health data is more critical than ever, especially with the widespread use of cloud technology in the healthcare sector. The protection of sensitive patient information is essential to maintain trust, compliance with regulations, and safeguard against potential threats.
Risks of Unprotected Health Data
Unprotected health data in the digital environment poses significant risks to patients, healthcare providers, and organizations. Without proper security measures, sensitive information can be vulnerable to unauthorized access, data breaches, identity theft, and ransomware attacks.
Consequences of a Data Breach
- Financial Loss: Healthcare organizations can face substantial financial losses due to fines, legal fees, and reputational damage following a data breach.
- Legal Ramifications: Violations of data protection laws can result in legal consequences, including lawsuits and penalties.
- Impact on Patients: Breached health data can lead to privacy violations, medical identity theft, and compromised patient care.
Impact of Insecure Health Data
According to a study by the Ponemon Institute, the average cost of a data breach in the healthcare industry is $7.13 million. Furthermore, research has shown that healthcare data breaches can have long-lasting effects on patient trust, with 37% of individuals stating they would switch healthcare providers after a breach.
Compliance Regulations and Standards
Compliance regulations and standards play a crucial role in governing the security of health data when utilizing cloud technology. Failure to adhere to these regulations can result in significant consequences for healthcare organizations.
HIPAA (Health Insurance Portability and Accountability Act)
- HIPAA is a key regulation in the United States that sets the standard for protecting sensitive patient data.
- Healthcare organizations must ensure that all electronic protected health information (ePHI) is securely stored and transmitted in the cloud.
- HIPAA compliance involves implementing technical safeguards, physical safeguards, and administrative safeguards to protect health data.
GDPR (General Data Protection Regulation)
- GDPR is a regulation in the European Union that governs the protection of personal data, including health information.
- Healthcare organizations operating in the EU must comply with GDPR when storing or transferring health data in the cloud.
- GDPR emphasizes the importance of obtaining explicit consent from individuals for data processing and ensuring data security measures are in place.
Importance of Compliance
- Complying with regulations such as HIPAA and GDPR is essential for healthcare organizations to protect patient confidentiality and maintain trust.
- Failure to comply with these standards can result in hefty fines, legal repercussions, and damage to the organization's reputation.
- By following compliance regulations, healthcare organizations demonstrate a commitment to data security and overall patient care.
Encryption and Data Protection
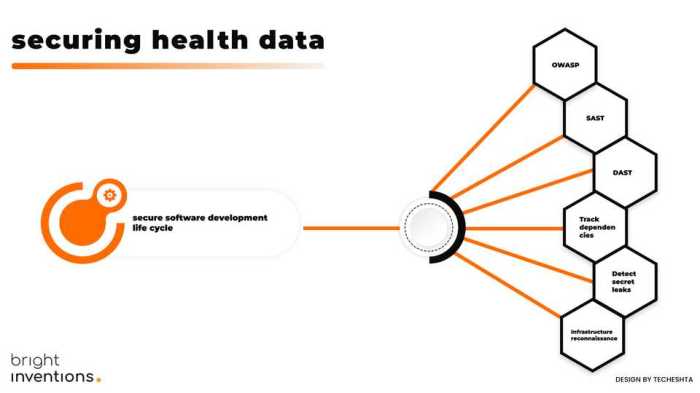
In today's digital age, securing health data is of utmost importance to protect patient privacy and comply with regulations. One crucial aspect of safeguarding sensitive information is through encryption and data protection.
Best Practices for Encrypting Health Data
- Utilize strong encryption algorithms such as AES (Advanced Encryption Standard) to secure health data stored on cloud servers.
- Implement encryption keys management to control access and ensure only authorized users can decrypt the data.
- Regularly update encryption protocols to address any vulnerabilities and maintain data security.
Examples of Encryption Methods
- End-to-end encryption: Ensures that data is encrypted from the sender's device until it reaches the recipient, preventing unauthorized access during transit.
- Transparent Data Encryption (TDE): Encrypts data at rest in databases to protect information stored on cloud servers from unauthorized access.
- SSL/TLS encryption: Secures data transmitted over networks, such as when accessing electronic health records (EHR) through a web browser.
Role of Encryption in Protecting Data
- At Rest: Encryption safeguards health data stored on cloud servers by converting it into unreadable ciphertext, ensuring confidentiality even if the data is accessed without authorization.
- In Transit: Encryption protects data as it is transmitted between devices or servers, preventing interception by cybercriminals and maintaining the integrity of the information being shared.
- Compliance: Encryption plays a vital role in meeting regulatory requirements such as HIPAA (Health Insurance Portability and Accountability Act) by ensuring that sensitive health data is adequately protected.
Access Control and User Authentication
Access control and user authentication are crucial components in securing health data in cloud environments. By implementing robust access controls, organizations can prevent unauthorized access to sensitive information, reducing the risk of data breaches and ensuring compliance with privacy regulations.
Methods of User Authentication
User authentication methods play a vital role in verifying the identity of individuals accessing health data. Some common methods include:
- Multi-factor authentication (MFA): Requires users to provide two or more forms of identification before granting access, such as a password and a unique code sent to their mobile device.
- Biometric authentication: Utilizes physical characteristics like fingerprints, facial recognition, or iris scans to authenticate users.
- Single sign-on (SSO): Allows users to access multiple applications with a single set of login credentials, streamlining the authentication process.
Managing User Permissions and Roles
Effectively managing user permissions and roles is essential for controlling access to health data. Organizations can implement the following strategies to ensure appropriate levels of access:
- Role-based access control (RBAC): Assigns permissions based on predefined roles within the organization, limiting access to only necessary information for each role.
- Regularly review and update user permissions: Periodically review and update user permissions based on changes in job roles or responsibilities to ensure that access rights remain relevant and appropriate.
- Implement least privilege principle: Grant users the minimum level of access required to perform their job functions, reducing the risk of unauthorized access to sensitive data.
Data Backup and Disaster Recovery
Regular data backups play a crucial role in ensuring the security and integrity of health data stored in the cloud. In the event of data loss, breaches, or system failures, having a robust disaster recovery plan in place is essential to minimize downtime and prevent permanent data loss.
Importance of Data Backups
Regular data backups are essential for protecting health information stored in the cloud. By creating backups at scheduled intervals, organizations can ensure that critical data is preserved and can be restored in case of accidental deletion, cyber attacks, or system failures.
Best Practices for Disaster Recovery Planning
- Establish a comprehensive disaster recovery plan that includes regular data backups, offsite storage, and testing procedures to ensure data can be restored quickly and accurately.
- Implement automated backup systems to streamline the backup process and minimize the risk of human error.
- Encrypt backup data to prevent unauthorized access and ensure data security during transmission and storage.
- Regularly test the disaster recovery plan to identify and address any weaknesses or vulnerabilities before a real disaster occurs.
Role of Backup Systems
Backup systems are critical for ensuring the availability and integrity of health data stored in the cloud. By creating redundant copies of data and storing them in secure locations, organizations can minimize the risk of data loss and ensure that critical information is always accessible.
Security Monitoring and Incident Response
In the healthcare industry, where sensitive patient data is constantly being transferred and stored in the cloud, the need for continuous security monitoring is paramount to safeguard against potential threats and breaches.
Real-time Threat Detection
Tools and technologies such as Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM) solutions, and threat intelligence platforms are commonly used for real-time threat detection in healthcare cloud environments. These tools help in identifying and responding to security incidents promptly.
Incident Response Protocols
When a security incident or breach occurs, having well-defined incident response protocols in place is crucial for minimizing the impact and preventing further damage. Organizations should have a documented plan outlining the steps to be taken, roles and responsibilities of team members, communication protocols, and procedures for containment, eradication, and recovery.
Final Review
In conclusion, the landscape of securing health data with cloud technology is multifaceted, requiring a harmonious blend of proactive measures and swift responses. By adhering to best practices and staying vigilant in the face of evolving threats, organizations can fortify their defenses and uphold the trust placed in them by patients and stakeholders alike.
FAQ Compilation
How important is data encryption for securing health data in the cloud?
Data encryption plays a critical role in safeguarding sensitive health information by converting it into unreadable code that can only be deciphered with the correct decryption key.
Why is compliance with regulations like HIPAA and GDPR essential for healthcare organizations?
Compliance ensures that health data is handled ethically, securely, and in accordance with legal requirements, fostering trust and accountability.
What are some key elements of an effective disaster recovery plan for health data in the cloud?
An effective disaster recovery plan should include regular data backups, clearly defined recovery procedures, and testing to ensure data integrity and availability in case of emergencies.